Email forwarding redirects incoming messages from one email address to a different email address. In this guide we show you how to setup Email Forwarders in your both your cPanel and Webmail. After that we take you through how to forward all email messages for a domain. What are Email Forwarders? If you have multiple email addresses for your business, …
Facing problem in using webmail? Don’t worry you can use the Gmail interface to send and receive emails with the email account you have created with your domain. You just need to setup your domain’s email address as a POP3 and SMTP account in your Gmail account. Gmail can be used as an email client. …
In this article, we will share a very simple JavaScript code snippet through which you can easily integrate your webcam into an HTML5 web page. Now, a day most of the website provides real-time webcam integration for profile picture upload or any account verification step. First, create an HTML DOM structure using the following code …
PuTTY’s copy and paste works entirely with the mouse. In order to copy text to the clipboard, you just click the left mouse button in the terminal window, and drag to select text. When you let go of the button, the text is automatically copied to the clipboard. You do not need to press Ctrl-C or Ctrl-Ins; in …
Please add below code in your .htaccess file. It works also in localhost and Live server. .htaccess file OR
Hello Friends Today We’ll discuss about Top 5 All Time Popular Wireless / WiFi Hacking Tools. You can use these popular wireless hacking packages and do penetration testing on your own wifi network whether your network is secure or hackable. I strongly recommend you to use Kali Linux OS because this OS has built-in software’s …
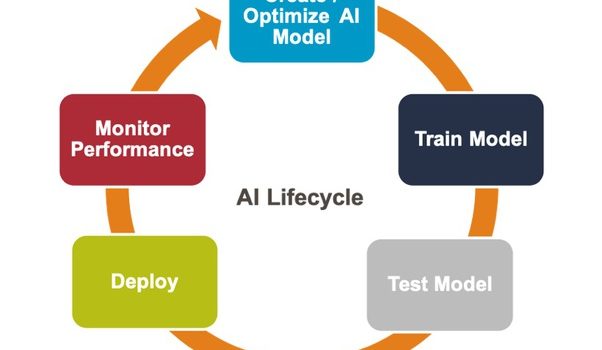
What is AI? AI (Artificial Intelligence) is the ability of a machine to perform cognitive functions as humans do, such as perceiving, learning, reasoning and solving problems. The benchmark for AI is the human level concerning in teams of reasoning, speech, and vision. Introduction to AI Levels Narrow AI: A artificial intelligence is said to …
CodeIgniter Session Management If you have developed desktop applications before then, you probably know that you can define a global variable assign a value to it and use it throughout the life cycle of the application opening and closing more than one (1) and each request will have access to the global variable. In other …
Email is very important in web applications. When a user signs up, we might want to send them an email to verify their email address and allow the user to confirm subscription. We also use email to reset forgotten passwords, send invoice and receipts to customers, etc. CodeIgniter makes it super easy for us to …