Google Authenticator is a two-step verification software used to keep your Google account and its related apps and programs more secure. You can download Google Authenticator as a smartphone app and use it when logging into Google apps and programs You should have two-factor authentication (2FA) turned on wherever you can, but there’s a more …
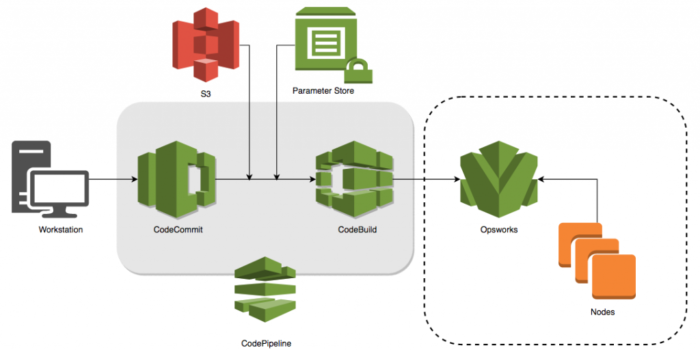
Introduction Amazon Web Services (AWS) has an extremely wide variety of services which cover almost all our infrastructure requirements. Among the given services, there is AWS Systems Manager which is a collection of services to manage AWS instances, hybrid environment, resources, and virtual machines by providing a common UI interface for all of them. Services …
Introduction Want to access the Internet safely and securely from your smartphone or laptop when connected to an untrusted network such as the WiFi of a hotel or coffee shop? A Virtual Private Network (VPN) allows you to traverse untrusted networks privately and securely as if you were on a private network. The traffic emerges …
The OpenVPN protocol is responsible for handling client-server communications. Basically, it helps establish a secure “tunnel” between the VPN client and the VPN server. When OpenVPN handles encryption and authentication, it uses the OpenSSL library quite extensively. Also, OpenVPN can use either UDP (User Datagram Protocol) or TCP (Transmission Control Protocol) to transmit data. If …
OpenVPN is both a VPN protocol and software that uses VPN techniques to secure point-to-point and site-to-site connections. Currently, it’s one of the most popular VPN protocols among VPN users. Programmed by James Yonan and released in 2001, OpenVPN is one of the only open-source VPN protocols that also has its own open-source application (SoftEther …
Bitcoin is a digital currency created in January 2009 following the housing market crash. It follows the ideas set out in a whitepaper by the mysterious and pseudonymous Satoshi Nakamoto.1 The identity of the person or persons who created the technology is still a mystery. Bitcoin offers the promise of lower transaction fees than traditional …
Here are some most common bad programming practices that every programmer should avoid to become a better programmer. 1. Giving up too soon Most of the programmers give up when they are very close to solution. So never lose hope and keep trying, you will definitely find a solution. 2. Acting defensively when someone critiques …
This article will guide you to choose the best laptop for programming in 2020. As a programmer or developer it becomes really confusing to pick a best laptop from thousands of laptops available in the market. It becomes even more difficult for a person who is just starting programming. Below I have shared some key …
Not so long ago, only a few people were considered computer programmers, and we viewed them with awe. In the digital age, we now live in; however, many IT jobs require a solid grasp of a programming language, and sometimes more than one. If you’re trying to advance in your career or change careers completely, …
We can create our own php.ini file in godaddy cpanel and other hosting too. We can increase upload_max_filesize, post_max_size, max_file_uploads, memory_limit, max_execution_time etc in php ini file in cpanel. So basically, Almost server like godaddy server, a2hosting server, hosting raja server that provide basic configuration in default php ini file. so some time we need …