Pune is one of India’s largest metropolitan cities and has been ranked as the 2nd most liveable city of India in “Ease of Living Index 2021.” Along with its twin city Pimpri Chinchwad (PCMC) and three cantonment towns of Camp, Khadki, and Dehu Road, Pune is the second major ‘IT Hub of India.’ PCMC, which …
Category : Tech News
51 posts
I recently implemented two factor authentication to secure administrator logins to something important. Doing so was much easier than I thought thanks to Google Authenticator and an open source composer package, so I thought I’d share this quick article to help others who might not have done it yet. What is Two Factor Authentication? 2FA …
How to Prevent Cross-site Scripting (XSS) – Generic Tips Preventing Cross-site Scripting (XSS) is not easy. Specific prevention techniques depend on the subtype of XSS vulnerability, on user input usage context, and on the programming framework. However, there are certain general strategic principles that you should follow to keep your web application safe. 1 Step …
You’ve launched your website and done all you can to ensure its success, but you may have overlooked a critical component: website security. Cyberattacks cause costly clean-up, damage your reputation, and discourage visitors from coming back. Fortunately, you can prevent it all with effective website security. We’ll discuss the basics of website security and what solutions will help ensure your …
Cross-site Scripting (XSS) Cross-site Scripting (XSS) is a client-side code injection attack. The attacker aims to execute malicious scripts in a web browser of the victim by including malicious code in a legitimate web page or web application. The actual attack occurs when the victim visits the web page or web application that executes the malicious …
What is a payment gateway and how does it work? A payment gateway is an application that makes the entire process of online payment more streamlined and secure. It acts as a secure link between your website or application and the bank. The role of payment gateway begins when a customer wishes to purchase on …
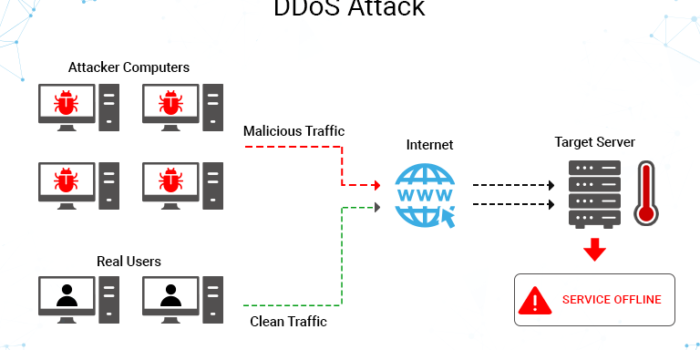
A Distributed Denial of Service (DDoS) attack is a non-intrusive internet attack made to take down the targeted website or slow it down by flooding the network, server or application with fake traffic. When against a vulnerable resource-intensive endpoint, even a tiny amount of traffic is enough for the attack to succeed. Distributed Denial of …
Introduction Want to access the Internet safely and securely from your smartphone or laptop when connected to an untrusted network such as the WiFi of a hotel or coffee shop? A Virtual Private Network (VPN) allows you to traverse untrusted networks privately and securely as if you were on a private network. The traffic emerges …
The OpenVPN protocol is responsible for handling client-server communications. Basically, it helps establish a secure “tunnel” between the VPN client and the VPN server. When OpenVPN handles encryption and authentication, it uses the OpenSSL library quite extensively. Also, OpenVPN can use either UDP (User Datagram Protocol) or TCP (Transmission Control Protocol) to transmit data. If …
OpenVPN is both a VPN protocol and software that uses VPN techniques to secure point-to-point and site-to-site connections. Currently, it’s one of the most popular VPN protocols among VPN users. Programmed by James Yonan and released in 2001, OpenVPN is one of the only open-source VPN protocols that also has its own open-source application (SoftEther …