What is a temporary email address? A temporary email address, also known as a disposable or throwaway email address, is a uniquely generated email alias designed for short-term usage. It gets automatically deleted once it has served its purpose or after a set time. Think about it as your alternative Gmail account that you use …
Category : Uncategorized
22 posts
Introduction Why Use a Fake Email Generator? TOP 5 Best Online Fake Email Generator Sites How to Choose the Best Fake Email Generator Conclusion
Shared Responsibility Model Advanced Cloud Security Challenges Zero Trust Security Zero Trust assumes no entity, internal or external, is inherently trustworthy. It advocates for: The 6 Pillars of Robust Cloud Security These practices provide a robust framework for securing cloud environments against a wide range of modern security threats, from unauthorized access to advanced persistent …
Cyber security is the practice of protecting computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It’s also known as information technology security or electronic information security. The Different Types of Cybersecurity Cyber security is a wide field covering several disciplines. It can be divided into seven main pillars: 1. Network Security …
In PHP 8, the money_format function has been removed. The recommended alternative is to use the number_format function in combination with the setlocale function to format currency values. Here’s an example: Note that you should set the locale to the appropriate value based on your requirements. The above example uses ‘en_US’ for US English formatting. …
Interview questions aim to check if applicants possess the skills to fulfill their responsibilities as PHP developers. Hence, you need to prepare questions that will allow the applicants to highlight their technical and behavioral skills. Here are some of the most asked PHP interview questions and sample answers: 1. Explain static and dynamic websites. What are their …
I have installed nodeJS on Ubuntu with following code Since I am a new user for ubuntu I also ran this code too Now when I type If you don’t like curl ... | sudo bash - then you can follow the manual instructions, which tells you how to add the Node.js repository to /etc/apt/sources.list.d/ yourself. NOTE: If you are …
One of my favorite features in Postman is the ability to write automated tests for my APIs. So if you are like me and you use Postman and you are tired of manually testing your APIs, this article will show how to harness the test automation feature provided by Postman. In case you don’t know …
Restoring a backup from a ZIP file – like the ones generated by our downloadable backup feature – can sometimes be a lengthy process. If you unzip a ZIP file locally on your computer before uploading the backup with SFTP, you’ll likely run into a bottleneck because SFTP can only transfer a limited number of files …
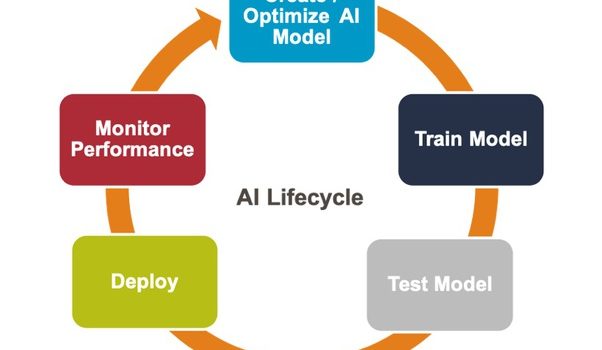
What is AI? AI (Artificial Intelligence) is the ability of a machine to perform cognitive functions as humans do, such as perceiving, learning, reasoning and solving problems. The benchmark for AI is the human level concerning in teams of reasoning, speech, and vision. Introduction to AI Levels Narrow AI: A artificial intelligence is said to …