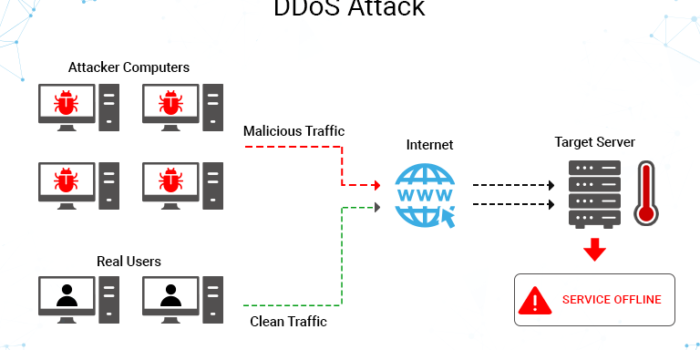
A Distributed Denial of Service (DDoS) attack is a non-intrusive internet attack made to take down the targeted website or slow it down by flooding the network, server or application with fake traffic. When against a vulnerable resource-intensive endpoint, even a tiny amount of traffic is enough for the attack to succeed.
Distributed Denial of Service (DDoS) attacks are threats that website owners must familiarize themselves with as they are a critical piece of the security landscape. Navigating the various types of DDoS attacks can be challenging and time consuming. To help you understand what a DDoS attack is and how to prevent it, we have written the following guide.
1.1 – Understanding a DDoS Attack
The objective of a DDoS attack is to prevent legitimate users from accessing your website. For a DDoS attack to be successful, the attacker needs to send more requests than the victim server can handle. Another way successful attacks occur is when the attacker sends bogus requests.
1.2 – How does a DDoS Attack Work?
The DDoS attack will test the limits of a web server, network, and application resources by sending spikes of fake traffic. Some attacks are just short bursts of malicious requests on vulnerable endpoints such as search functions. DDoS attacks use an army of zombie devices called a botnet. These botnets generally consist of compromised IoT devices, websites, and computers.
When a DDoS attack is launched, the botnet will attack the target and deplete the application resources. A successful DDoS attack can prevent users from accessing a website or slow it down enough to increase bounce rate, resulting in financial losses and performance issues.
1.3 – What is the Goal Behind a DDoS Attack?
The main goal of an attacker that is leveraging a Denial of Service (DoS) attack method is to disrupt a website availability:
- The website can become slow to respond to legitimate requests.
- The website can be disabled entirely, making it impossible for legitimate users to access it.
Any type of disruption, depending on your configuration, can be devastating to your business.
Skip to section 4 to learn some of the reasons why.
1.4 – What is the Difference Between DoS and DDoS Attacks?
Denial of Service (DoS) attacks and Distributed Denial of Service (DDoS) attacks are very similar. The only difference between them is their scale. Single DoS attacks come from one source, while DDoS (distributed) attacks come from multiple locations, often spoofed.
Whether a DoS or DDoS attack, the attacker uses one or more computers. DoS attacks are on the lower end of that spectrum while DDoS attacks are on the higher end. Very large DDoS attacks can span hundreds or thousands of systems. The proliferation of DoS/DDoS attacks are directly attributed to the proliferation of DDoS-for-hire services market, also known as Booter Services.
1.5 – Can DDoS Attacks Steal Information?
DDoS attacks cannot steal website visitors information. The sole purpose of a DDoS attack is to overload the website resources. However, DDoS attacks can be used as a way of extortion and blackmailing. For example, website owners can be asked to pay a ransom for attackers to stop a DDoS attack.
DDoS attacks can have many other motivations including political, hacktivist, terrorist, and business competition. Anyone with a financial or ideological motive can damage an organization by launching a DDoS attack against it.
1.6 – What Are the Signs of a DDoS Attack?
The signs of DDoS attacks include:
- The website is responding slowly.
- The website is unresponsive.
- The user has problems accessing the website.
- Internet connection issues if you are a target.
Any type of disruption, depending on your configuration, can be devastating to your business.
1.7 – The Amplification Effect of DDoS Attacks
Every time we talk about DDoS attacks, we have to mention its amplification effect. In order to achieve amplification, most attackers leverage botnets consisting of compromised computers, allowing them to amplify their attack across the size of the botnet. One attacker can control 1,000 bots which can then be used to DDoS the victim. That’s 1,000 bots vs. 1 server, making it easier for the attacker to win. However, not always do attackers need to be in control of the botnets. They can also make a host send a response to a wrong destination. For example, vulnerable memcached servers were used to take Github down and none of them were actually hacked, only fooled by the attacker.
The other aspect of amplification has to do with the network layer and spoofed requests. What if each computer on the botnet only needs to send 1 byte to get a 100 byte response? That’s called a 100x amplification. When the request is spoofed, the reply goes back to someone else on the internet, not the attacker. This means that the network port of the server is processing the 1 byte incoming + 100 bytes outgoing, while the attacker only processes the 1 byte outgoing on their end.
A theoretically small botnet of 1,000 bots can easily generate close to 100 Gbps when using the right amplification method.
Amplification does not stop there. Most people tend to think of them only in terms of Gigabytes of network, but there is also something happening at the application layer.
What if, with just 1 HTTP request from the botnet the attacker can force a web application to do a lot of work? Like an expensive search or something that takes lots of resources? That’s the basis of many Layer 7 (HTTP flood) attacks that we see.
Note
Can you imagine how hard it is for most servers to handle a DDoS attack?
We are talking about:
- Thousands of bots,
- sending hundreds of requests per second,
- with network-layer amplification.
1.8 – What Happens During a DDoS Attack?
Have you ever wondered what happens during a DDoS attack and what it looks like on the technical side?
A DDoS attack depletes the server resources and increases the website load time. When a DDoS attack hits a website, it may suffer performance issues or crash the server completely by overwhelming the server’ resources such as CPU, memory or even the entire network. Most DDoS attacks today originate from a hacker-controlled botnet of vulnerable IoT devices. This includes internet connected security cameras, household appliances, smart TVs, home lighting systems, and even refrigerators.
The exponential growth of DDoS attacks is mostly due to the total lack of regulatory control over IoT devices, which makes them excellent recruits for the botnets. A hijacked group of IoT devices with unique IP addresses can be redirected to make malicious requests against websites, causing a DDoS attack.

Trackback 20